
Enhance the Security and Performance of your Managed Databases with Private Networks
Compared to an on-premise, self-managed Database, a fully Managed Database can help you save time and drastically reduce infrastructure setup and management costs.

Good news! The Virtual Private Cloud (VPC) is coming, and Private Networks (PN) are going regional. While you could previously use a private network to connect all your resources within a single Availability Zone (AZ), you’ll soon be able to do this across all AZs within the same Region. We’re currently in a migration phase, but eventually, regional Private Networks will replace zonal Private Networks entirely.
The VPC will allow you to build your own virtual private clouds on top of Scaleway’s shared public cloud. This keeps your resources secure and isolated from the public internet. And, of course, it’s included for free with all Scaleway accounts.
The Virtual Private Cloud is currently still being rolled out in public beta. The feature is going to be made available to all Scaleway customers soon. But if you can’t wait, you can still join the public beta.
Update July 2023: Scaleway’s Virtual Private Cloud is now available for all accounts!
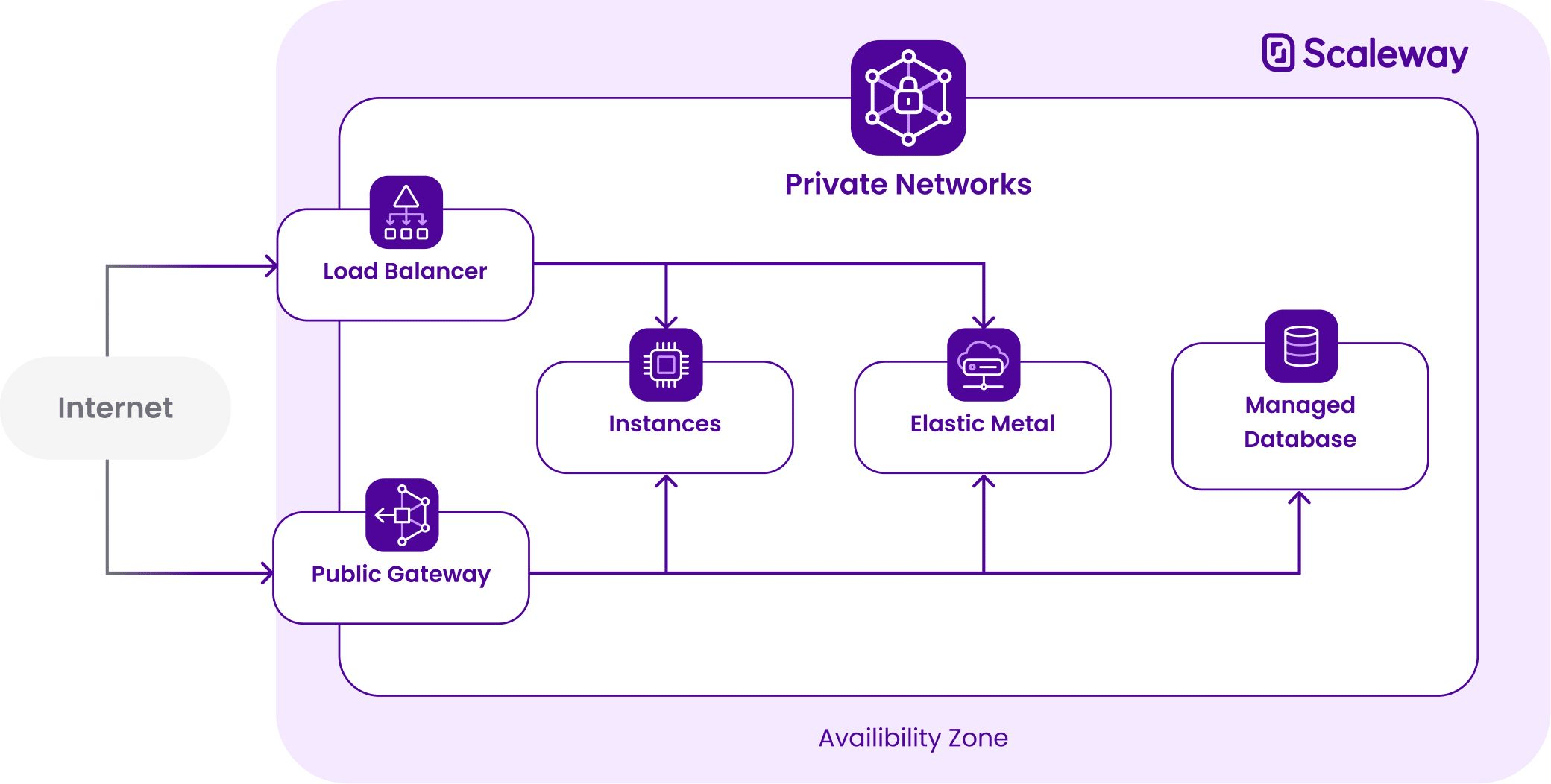
A private network lets you isolate resources from the internet in a secure and private network, like connecting different resources on a single isolated switch.
This is very similar to the switch part of your internet box at home, which isolates your computers attached to it in a private network. All your computers and connected objects (voice assistant, printer, etc.) can communicate with each other on a secure network and rely on the box to communicate with the internet.
A private network in the cloud has a function similar to your WiFI network at home, letting all resources inside it communicate securely.
Today, instances have access to a zonal private network to communicate securely. Zonal means you can only attach resources from the same Availability Zone to the network.
With the public VPC beta, we are introducing regional Private Networks, so resources from the same Region can communicate securely.
A Region is a geographical area such as France (Paris: fr-par) or the Netherlands (Amsterdam: nl-ams) in which Scaleway products and resources are located. A Region contains multiple (a minimum of three) Availability Zones, and AZs must not be located in the same building. The latency between multiple AZs of the same Region is low, as they have a common network layer.
Previously, different AZs of the same Region had to communicate through the internet, which is not secure by default. You could make the communication secure, but it required a manual setup that wasn’t easy.
By making Private Networks regional, resources from the three AZs of the PAR region (Par1, Par2, Par3), for example, can now communicate securely.
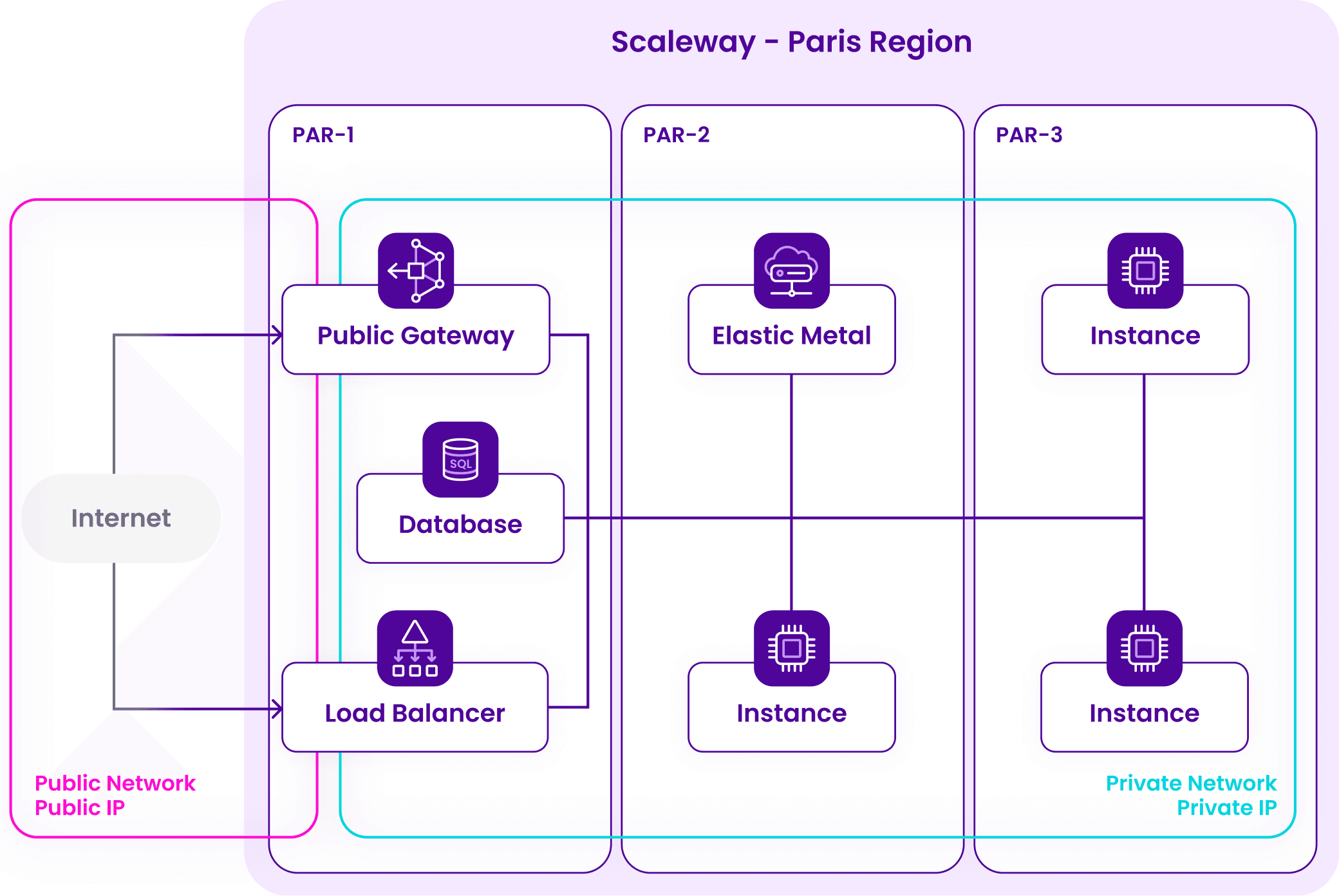
Regional Private Networks will eventually replace the original Private Networks, but anything you could do with zonal PNs, you can do with regional PNs — except better.
There are many reasons we are migrating Private Networks from AZs to Regions. For one, it’s good practice to spread the risk with machines in different Availability Zones to mitigate the risk of one AZ failing.
It also greatly simplifies resource management and allows for the development of resilient and secure architectures. You can connect a large number of resources from various Scaleway cloud ecosystem products and easily scale your infrastructure based on your needs.
It also allows regionally managed products, such as Kapsule, to isolate cluster nodes into a secure private network and privately communicate with other resources attached to this PN (for example, a managed database), which was a long-awaited network capability.
Common use cases for regional Private Networks are:
Virtual Private Cloud is a new managed product in the Network products family. It’s a regional product covering all the AZs of a Region. A VPC can contain multiple Private Networks — like a group of PNs inside a region.
The VPC ensures that PNs inside it have no overlapping CIDR blocks so that the IP ranges of the PN subnets do not overlap each other. It enables automatic IP addresses and routes configuration within the private network thanks to a DHCP server and an internal DNS zone.
At the moment, the Virtual Private Cloud sounds like an empty box, but it is, in fact, the important foundation for various advanced network-managed features we plan to add. For example, we want to enable PNs inside a VPC to communicate with each other thanks to managed routing capability — a feature that will be implemented soon —, and Access Control Lists.
It also adds connectivity capabilities between VPCs, such as:
During the public beta, original zonal PNs and regional PNs will temporarily coexist. You can create as many regional Private Networks as you want, but only from the console for now. These PNs can be attached to only one default VPC per Region.
You can still attach all the same resources to your Private Networks as you could when they were still zonal: Instances, Databases, Load Balancers, Public Gateways, and Elastic Metal. However, you can now also attach your Kapsule clusters to your Private Networks or directly create a new Private Network on the go during the Kapsule cluster creation process.
We will progressively migrate all current zonal Private Networks to regional Private Networks, which will automatically be attached to a newly created default VPC. This will be fully transparent for users, with no actions required.
And here’s what will change once the VPC has been launched for all customers:

Compared to an on-premise, self-managed Database, a fully Managed Database can help you save time and drastically reduce infrastructure setup and management costs.
To launch an application in the cloud, you need to be able to access the servers on which it is hosted. We will learn how to do that in this article.
How to leverage the benefits of both the public and the private cloud? How to build a IaaS infrastructure on top of dedicated servers that fits your cloud ecosystem and processes?