Centralize management
Create and manage your cryptographic keys in seconds. Abstract away complex and error-prone cryptographic operations and ensure strong data encryption with full lifecycle control.
Automate your encryption keys management to reach another level of security
Create and manage your cryptographic keys in seconds. Abstract away complex and error-prone cryptographic operations and ensure strong data encryption with full lifecycle control.
Symmetric or asymmetric encryption, Key Manager masters all protocols to comply with the most demanding regulations, such as ISO27001 and HDS.
Key Manager offers another layer of security to your application. With the tracability provided by Audit Trail and the access mamagement from IAM you're architecture is armed with bulletproof security.
Key Manager provides all essential cryptographic functions needed to secure your applications. This allows you to easily protect data, ensure its integrity, and verify identities with operations including:
Key Manager utilises AES-256-GCM, a fast and efficient symmetric encryption algorithm perfect for securing large volumes of data. Since the same key is used to both lock and unlock the data, protecting it is the top priority. Our service ensures this key remains protected and confidential, allowing you to leverage its high performance without the operational risk.
This method uses a public key to encrypt data and a separate, secret private key to decrypt it. This powerful design is ideal for secure communication and digital signatures, as you never need to share the key that unlocks your data. Key Manager supports multiple RSA-OAEP-SHA256 key strengths:
The strength of your encryption is only as good as the security of your keys. Key Manager provides a single, secure platform to handle the entire key lifecycle — from generation and rotation to secure deletion. This removes the operational burden and risk of manual key handling, ensuring your data remains protected.
| Name | Price |
|---|---|
| Symmetric & Asymmetric Key storage | €0.04 monthly per key version |
| Symmetric & Asymmetric Key operation | €0.03 per 10 000 requests |
| Restore Key operation | €0.01 per key restored |
Your keys are stored and processed exclusively in our European datacenters.
No complex billing formulas or hidden API call charges. We offer a straightforward, pay-as-you-go model so you can secure your infrastructure without worrying about a surprise bill.
We believe powerful security measures shouldn’t be complicated. With a clean API and clear documentation, you can integrate robust encryption into your applications rapidly.
Gain granular control over data security by implementing application-layer encryption. Use the Key Manager API directly within your code to encrypt specific sensitive fields – Such as personal information, financial data or user credentials – before they are ever written to your database or object storage. This ensures the data remains opaque everywhere except within your trusted application logic.

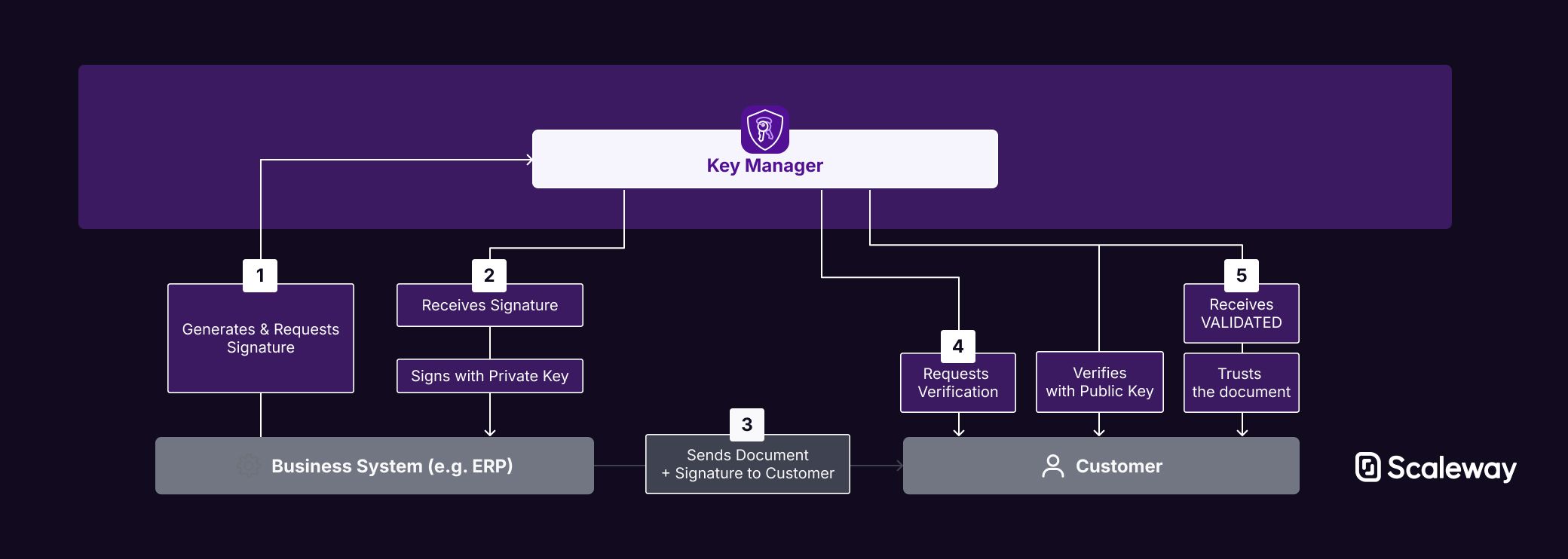
Automatically sign business documents like invoices, contracts, or financial reports to guarantee their authenticity. When you send a signed document, your customer or partner can use your public key to verify it originated from you and has not been altered. This builds trust, prevents fraud, and establishes a secure and verifiable record of your documents.


Key Manager strengthens your security by centralizing control over all your encryption keys. It handles the complex, error-prone cryptographic operations for you, which significantly reduces the risk of accidental key exposure or misuse. This allows you to implement strong encryption best-practices without the cost and complexity of building and maintaining your own key infrastructure.
Scaleway's Key Manager has one Root Encryption Key ("REK") per region, which is securely stored in our facilities. By design, your key material can never be exported or viewed in plaintext – not even by Scaleway employees. More information is available in the dedicated documentation page.
Secret Manager is designed to store and manage complete secrets, like database passwords or API tokens. Key Manager is built specifically to manage the lifecycle of raw cryptographic keys themselves. The crucial difference is that keys never leave Key Manager; you ask the service to perform an encryption or decryption operation for you, which is a more secure model. More information is available in the dedicated documentation page.
Deleting a key is a destructive action that makes data unrecoverable, so we've built in a safety net. When you initiate a deletion, the key is first disabled for 7 days (it enters the state of “Scheduled for Deletion”). During this time, the key cannot be used but can be restored. After the grace period ends, the key material is permanently and irreversibly destroyed.