Customer Success Story : Cloud IAM

Cloud-IAM Challenges
At Cloud-IAM, for every customer’s deployment, we create a dedicated infrastructure including DNS, multiple instances, managed databases, networks with VPC and public gateway. All that has been automated using the terraform provider.
It only takes a few minutes before a complete Cloud-IAM Keycloak IAM deployment becomes available to our customers.
We managed to get the same level of automation with Scaleway than we have with the other major Cloud providers, but moreover, we can guarantee our customers that their data are kept safe in Europe.
How we overcame challenges
What products are used :
Instances : We heavily use Elements to create servers in all available regions.
Managed Database : In order to provide Postgres databases in HA mode with scalable storage.
VPC, Private Network and Public Gateway : In order to keep everything private and reduce the attack surface of our servers. The embedded SSH bastion of the Public gateway is also a “nice to have” feature.
Object Storage : This is our multi purpose component. The Object Storage enables us to store all the extensions uploaded by our clients to customized their Cloud-IAM deployments, as well as storing our cold backups, sharing publicly our legal documents, storing in highly available all our internal monitoring stack. The different Policies help us to keep storage fees low with the Glacier storage through time.
Load Balancer : Even if we deploy our own load balancer for customers’ deployment, we also use Scaleway Load Balancer for easier management of some part of our internal stack.
Cockpit : We are planning to switch our self hosted monitoring stack to use the managed Grafana/Prometheus/Loki of Cockpit but right now it enables us to consume all metrics of our deployed components (Instances, Databases) in an easier manner than we did before.
Containers : We use Containers to easily deploy some of our side components like the documentation of our product or some tools for dedicated clients.
DNS : Since we make great use of automation the DNS component helps us to also, the use of DNS failover with health or geoIP enables us to operate all of our infrastructure with greater availability.
Secret Manager : As the service is quite new, we are analyzing how we can benefit from it and maybe reduce our cost on our configuration’s vault infrastructure.
How did we build our architecture at Cloud-IAM
We use several tiers architecture with a segregated network to enforce the security of our customers’ deployments. Everything is built using Scaleway’s terraform provider, as well as other tools like the Ansible dynamic inventory, the CLI and the API. All of these have been a very important part of the decision for us to choose Scaleway as a European Cloud provider.
Why we did not choose the competitors?
We are a multi cloud SaaS so Cloud-IAM also enables users to deploy their Identity and Access Management Clusters to Amazon Web Services, Google Cloud Platform and 3DS Outscale.
Customer technical architecture - diagram:
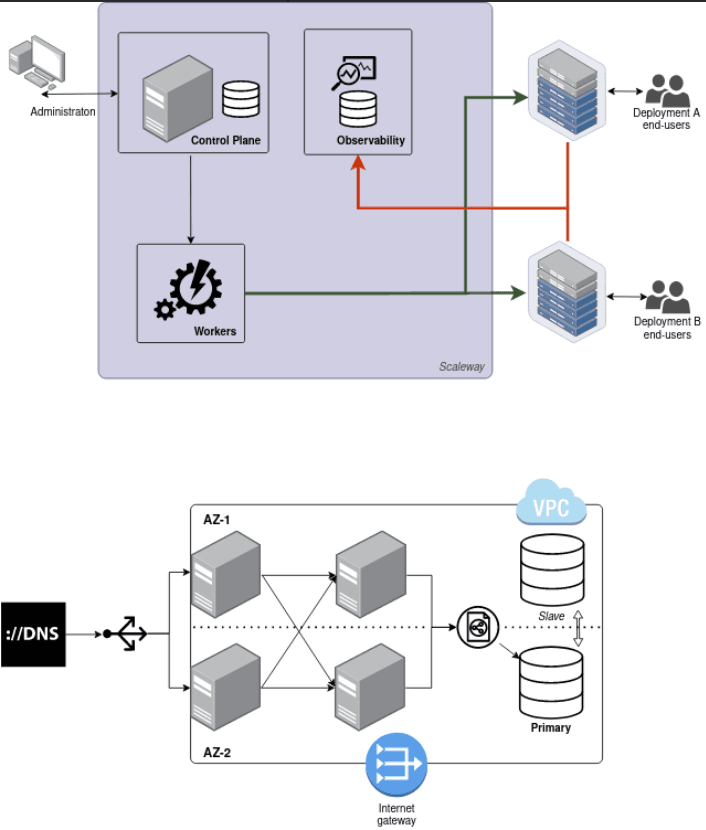
You can find our architecture insight in our public documentation
Managed IAM Deployment creation:

IAM deployment details:

Results of collabaration between Cloud-IAM and Scaleway
+500 servers managed automatically;
+600 dns entries;
A complete managed IAM deployment, including servers, database, dns, network is spawned in less than 10 minutes (half the time than AWS for instance);
More 2 000 deployment hosted by Scaleway;
99,998% average up time last year;