How to manage access to your Managed Inference deployments
You can manage and restrict access to your Managed Inference deployments via the following methods:
- Enable or disable authentication by API key
- Use IAM features to control which API keys are accepted and under what conditions (including IP-based restrictions)
- Remove your deployment's public endpoint, and allow controlled access only via Private Networks
Read on for full details.
Before you start
To complete the actions presented below, you must have:
- A Scaleway account logged into the console
- A Managed Inference deployment
- Owner status or IAM permissions allowing you to perform actions in the intended Organization
How to enable or disable authentication by API key
By default, when you create your Managed Inference deployment, authentication by API key is automatically enabled. This means that when the deployment is accessed via either its public or private endpoint, a valid Scaleway API key must accompany all requests.
You can disable API key authentication at any time, for either the public endpoint, the private endpoint, or both.
- Click Managed Inference in the AI section of the Scaleway console side menu. A list of your deployments displays.
- From the drop-down menu, select the geographical region containing your deployment.
- Click the deployment whose authentication you want to manage. The deployment's dashboard displays.
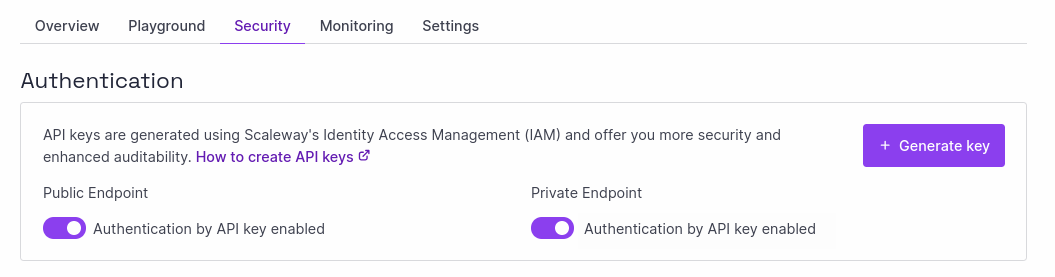
- Click the Security tab.
- In the Authentication panel, use the toggles toggle icon to enable or disable authentication by API key for the public and/or private endpoint.
How to manage access to a deployment with IAM
When authentication by API key is enabled, a valid Scaleway API key must accompany all requests sent to your deployment's endpoint.
An API key is considered valid to access a deployment when:
- It belongs to the Owner of the Organization which owns the deployment, or
- It belongs to a Member or Application of the Organization which owns the deployment, and the Member/Application has appropriate IAM permissions.
There are two IAM permission sets specific to Managed Inference deployments: InferenceFullAccess (allowing access to create, read, update, and delete a deployment) and InferenceReadOnly (allowing read-only access). Alternatively, wide-scoped permission sets such as AllProductsFullAccess will also allow access.
Permissions are attributed via policies, which are then attached to a Member or Application.
You can further restrict access by imposing conditions when defining a policy. This enables you to allow access only to authorized API keys when presented by specific user agents (e.g., Terraform), from certain IP addresses, or during defined dates and times.
How to manage deployment access as an Organization Owner or Administrator
- Invite Members (other humans) to your Organization, or create Applications (non-human users).
- Create and attach a policy to the Member or Application, defining the permissions they should have in your Organization by selecting permission sets (e.g.
InferenceFullAccess). If desired, define conditions as part of the policy, to further restrict access based on user agent type, date/time or IP address.
All API keys generated by the Member, or for the Application, will automatically inherit the permissions you defined, and can be used to access a Managed Inference deployment's endpoint depending on those permissions.
You can revoke access to a deployment at any time by modifying or deleting the policy attached to the Member or Application in question.
How to access a deployment as an Organization Member
Your access to Managed Inference deployments owned by an Organization in which you are a Member depends on the IAM permissions attributed to you by the Organization's Owner or administrators.
Your permissions will be automatically applied to any API keys you generate for yourself in the Scaleway console. Check with your Organization Owner if you are unsure that you have the right permissions to access a Managed Inference deployment.
- Log into the Scaleway console and generate an API key for yourself.
- Use this API key for authentication when sending requests to a Managed Inference deployment.
How to restrict access over Private Networks
For enhanced security, you can remove your deployment's public endpoint, attach it to a Private Network, and allow access only via its private endpoint. Only resources within the Private Network's VPC will be able to access the deployment, and they must have downloaded the resource's TLS certificate.
You can still require API key authentication via the private endpoint, and use the methods described above to fine-tune API key restrictions and access. In addition, you can also use VPC features such as Network ACLs for enhanced control and security.
- Create your deployment without checking the Allow public connections box, or remove the public endpoint via its Overview screen in the console if you already created it with a public endpoint.
- Ensure the deployment is attached to a Private Network.
- Transfer the deployment's TLS certificate to the resources in the VPC that need to access the deployment.
- (Optional) Ensure that API key authentication is enabled, and use policies to define IAM-based rules and conditions for access.
- (Optional) Use VPC features such as Network ACLs to place IP-based restrictions on which resources in the VPC can access the deployment.
- Follow the instructions in the dedicated documentation for sending requests to your deployment in a Private Network.