Understanding VPC routing
Overview
VPC routing allows resources and Private Networks in the same VPC to communicate with each other via automatically-created managed routes, and user-defined custom routes.
When you create a Private Network, a managed route is automatically created and added to the VPC’s route table. This route allows the VPC to automatically route packets to resources attached to that Private Network, even if they originate from a resource attached to a different Private Network on the VPC.
Managed routes are also automatically added to the VPC’s routing table when you attach a Public Gateway to a Private Network, and tell it to advertise the default route. This type of managed route allows traffic to be forwarded to addresses outside the VPC (i.e. the public internet) via the Public Gateway.
You can create your own custom routes to send traffic for defined IP ranges towards a specified resource in the VPC, for example if you want to route to a VPN installed on an Instance.
Routing is activated by default whenever you create a new VPC, and can be activated on pre-existing VPCs by following these steps. Network ACLs, to finely control and filter VPC traffic, are available via the API (currently in Public Beta).
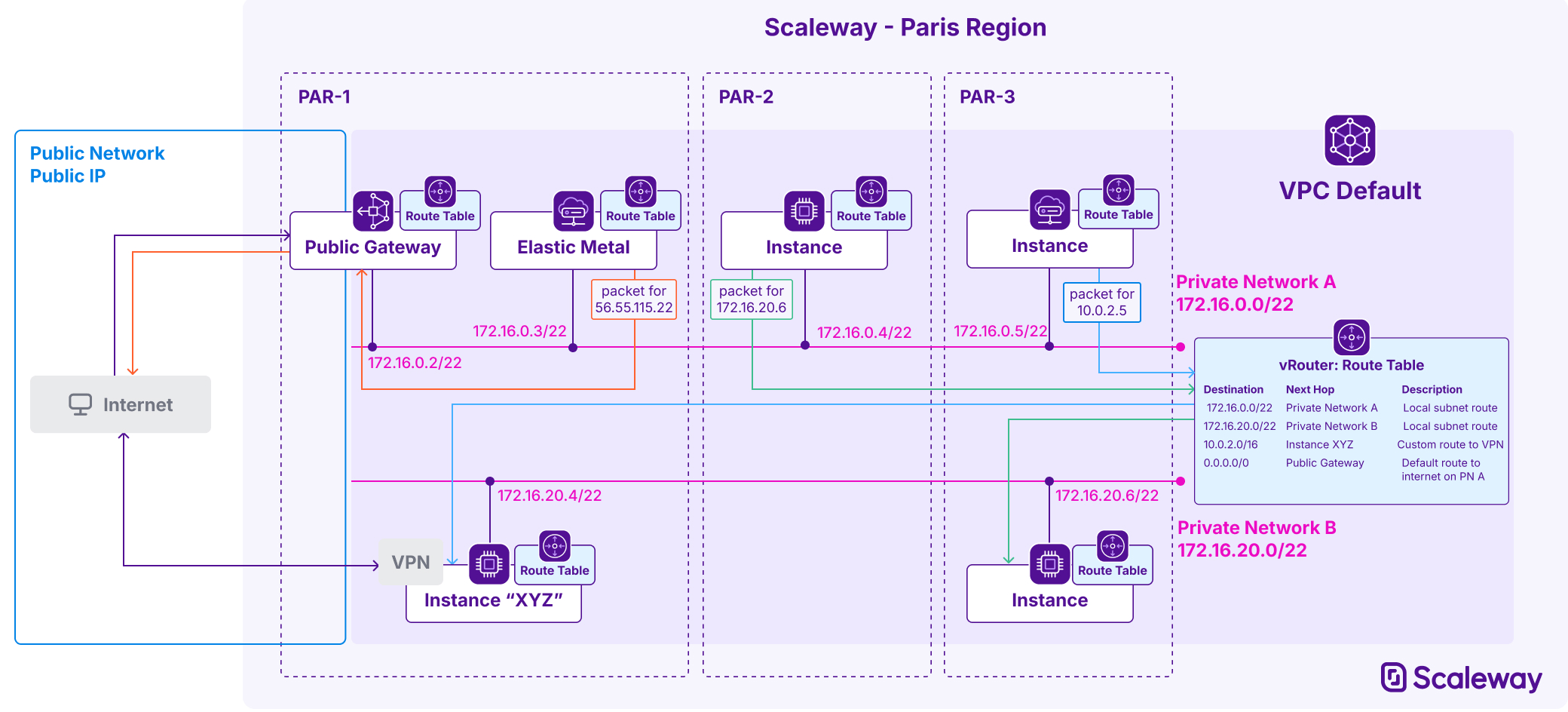
The diagram below shows an example of how routing works across two Private Networks on a VPC. The route table is held on the VPC's virtual router (VRouter), and synched to each resource as it joins a Private Network.
- An Elastic Metal server on Private Network A can send a packet to the public internet via a Public Gateway also attached to Private Network A.
- An Instance also on Private Network A can send a packet to an Instance on Private Network B, via the vRouter.
- The same Instance on Private Network A can send a packet to an IP destination at the other end of the VPN hosted on Instance XYZ on Private Network B, thanks to a custom route.
Route table
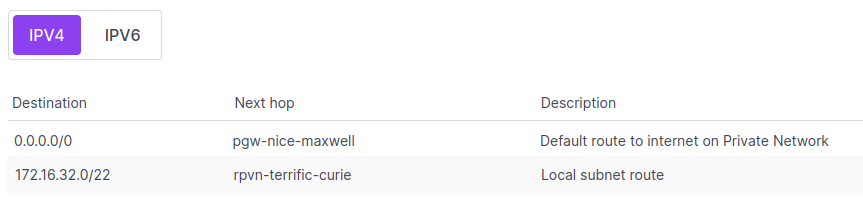
Every VPC has an associated route table, used to manage and control the routing of traffic within the VPC. The routes within a route table tell the VPC where to send traffic trying to get to a specific destination IP address. One line in the route table corresponds to one route. A route consists of:
- A destination IP or IP range. This specifies that the route applies to traffic with a matching destination IP.
- A next hop. This specifies where the VPC should forward traffic that is trying to reach the destination IP.
- For local subnet routes, the next hop will be the relevant Private Network. Traffic destined for an IP within the CIDR block of the Private Network's subnet will find the attached resource there.
- For custom routes, the next hop is a defined resource on a defined Private Network.
- If the destination IP is not known on the VPC (represented by the
0.0.0.0/0address), its next hop will be a Public Gateway so that it can reach the public internet (as long as a Public Gateway set to advertise the default route has been attached to the Private Network).
- A description. This helps to describe the type of route, e.g.
Local subnet routefor routes to Private Networks, orDefault route to internetfor routes to Public Gateways, or a user-defined description for custom routes. - A scope. This shows whether teh route is advertised across the entire VPC, or (in the case of default routes), only certain Private Networks.
When deciding which route to apply, the route table reads the routes from most specific to least specific, in terms of destination IP range. The first matching route encountered is the one that determines the path for the traffic. Therefore, a route to destination 172.16.8.0/22 is applied before a default route to 0.0.0.0/0.
Scaleway VPC routing supports both IPv4 and IPv6 protocols. Managed routes to Private Networks (local subnet routes) are simultaneously generated for both IPV4 and IPV6, and both are added to the route table. As Public Gateways do not support IPv6, routes to them are generated for IPv4 traffic only. Custom routes are only created for the IP type specified during the creation process. When reading your route table, a toggle allows you to switch between the default view of IPV4 routes, to an alternative view of IPV6 routes.
A VPC's route table displays in the Routing tab of the console. The route table is populated with routes when you either create a custom route,or create a Private Network in the VPC, or attach a Public Gateway to a Private Network and set it to advertise a default route.
Usage considerations
Bear in mind the following when activating VPC routing:
- Once activated on a given VPC, routing cannot be deactivated on that VPC.
- When routing is activated, all Private Networks on the VPC can communicate.
- Network ACLs, to finely control and filter traffic within a VPC, are in Public Beta and currently available via the VPC API only. Alternatively, users may choose to configure NACLs directly on certain resources (e.g. Instances, Elastic Metal servers) using tools such as
iptablesornftables. - The scope of route advertisements for custom routes and default routes to Public Gateways depends on when you created your VPC, and/or whether you have updated its routing behavior to the most recent version. Read the full documentation below for details.
Best practices
We recommend that you build your VPC infrastructure with separation of concerns in mind. Separation of concerns is a fundamental design principle aimed at breaking down large complex systems into smaller, distinct components each with clear responsibilities and interfaces. This kind of design will future-proof your VPC and come into its own when we introduce features such as custom routing and ACLs.
Separating resources into different Private Networks according to function and usage can:
- Improve network performance by reducing broadcast traffic and congestion
- Enhance manageability via a logical organization of resources
- Enable easier troubleshooting, monitoring and maintenance
- Allow for easier scalability
For example, you may use one Private Network for frontend resources and another for backend resources, limiting public access only via Load Balancers and/or Public Gateways.
Updating routing behavior
From July 1st 2025, new routing behavior is available for VPCs.
- This routing behavior will be applied automatically to VPCs created after July 1st 2025, or to pre-existing VPCs that only activate routing after this date.
- Pre-existing VPCs already using routing must be updated to accept this new behavior
| Old behavior | New behavior | |
|---|---|---|
| Custom routes | Custom route advertisements are scoped only to the Private Network(s) to which the “next hop” resource is directly attached. | Custom route advertisements are scoped to the entire VPC as standard. |
| Default routes | Public Gateways' default route advertisements are scoped only to the Private Network(s) to which the gateway is attached. Private Networks cannot receive default route advertisements from Public Gateways they are not directly attached to. | Standard behavior remains unchanged, but now each Private Network can opt in to receive default route advertisements from across the entire VPC. |
Custom routes
Previously, custom routes were scoped only to the Private Network(s) of the “next hop” resource. Their routes were not propagated to other Private Networks in the VPC. For example, in the scenario of using a custom route to route traffic towards a VPN tunnel, the origin of the packet had to be in the same Private Network as the resource hosting the VPN.
With new routing behavior, custom routes are scoped to the entire VPC as standard. All Private Networks in the VPC receive route advertisements for all custom routes. This gives enhanced flexibility when using custom routes to route traffic towards VPN tunnels.
You can configure Network ACLs via the VPC API if you want to restrict traffic flow along custom routes.
Default routes
Previously, Public Gateways could only advertise their default routes to the Private Networks to which they were directly attached. Resources on other Private Networks within the VPC could not access the public internet via these remote Public Gateways.
With new routing behavior, this standard behavior remains unchanged. Default routes' scope is still, as standard, limited to their directly attached Private Networks.
However, you now have an additional option to enable each Private Network to receive advertisements of all default routes throughout the entire VPC. This includes routes towards all Public Gateways advertising a default route, as well as any custom-created default routes. This allows resources on other Private Networks to find access to the public internet, even if they do not have their own attached gateway.
See the documentation on how to manage default route scope for a given Private Network, once you have updated to new routing behavior.
Granularity
The option to receive all default route advertisements must be enabled on a per-Private-Network basis.
This means that each Private Network in a VPC can opt to either receive only default routes from directly attached Public Gateways (and local custom default routes, if they exist), or all default routes being advertised throughout the whole VPC.
If you wish to exercise more granular control over default route advertisements, we recommend that you configure Network ACLs via the VPC API.
Multiple default routes
When a resource on a Private Network receives multiple default route advertisements, the default route that is ultimately used will depend on the resource's OS and configuration. For a resource running Ubuntu, it is likely that the first default route advertisement received will be prioritized.
Impact on existing setup
When you update to new routing behavior, the only automatic change is that your custom routes (if any) will now be advertised across the whole VPC.
Your Private Networks will continue to receive only their local default route announcements, unless you enable Receive all default route announcements in each Private Network's settings. Therefore, there is no risk of the scope of default route announcements automatically changing without your specific intervention, even after updating to new routing behavior.
Your existing setup may be impacted by the new behavior if you want your custom routes to be scoped only to the next-hop resource's Private Network. In this case, we recommend that you use Network ACL rules via the VPC API to limit access to the custom route.
Example use of NACLs to mitigate impact
The example below shows how to achieve the desired routing behavior for a custom route which is now advertised across the whole VPC.
Scenario
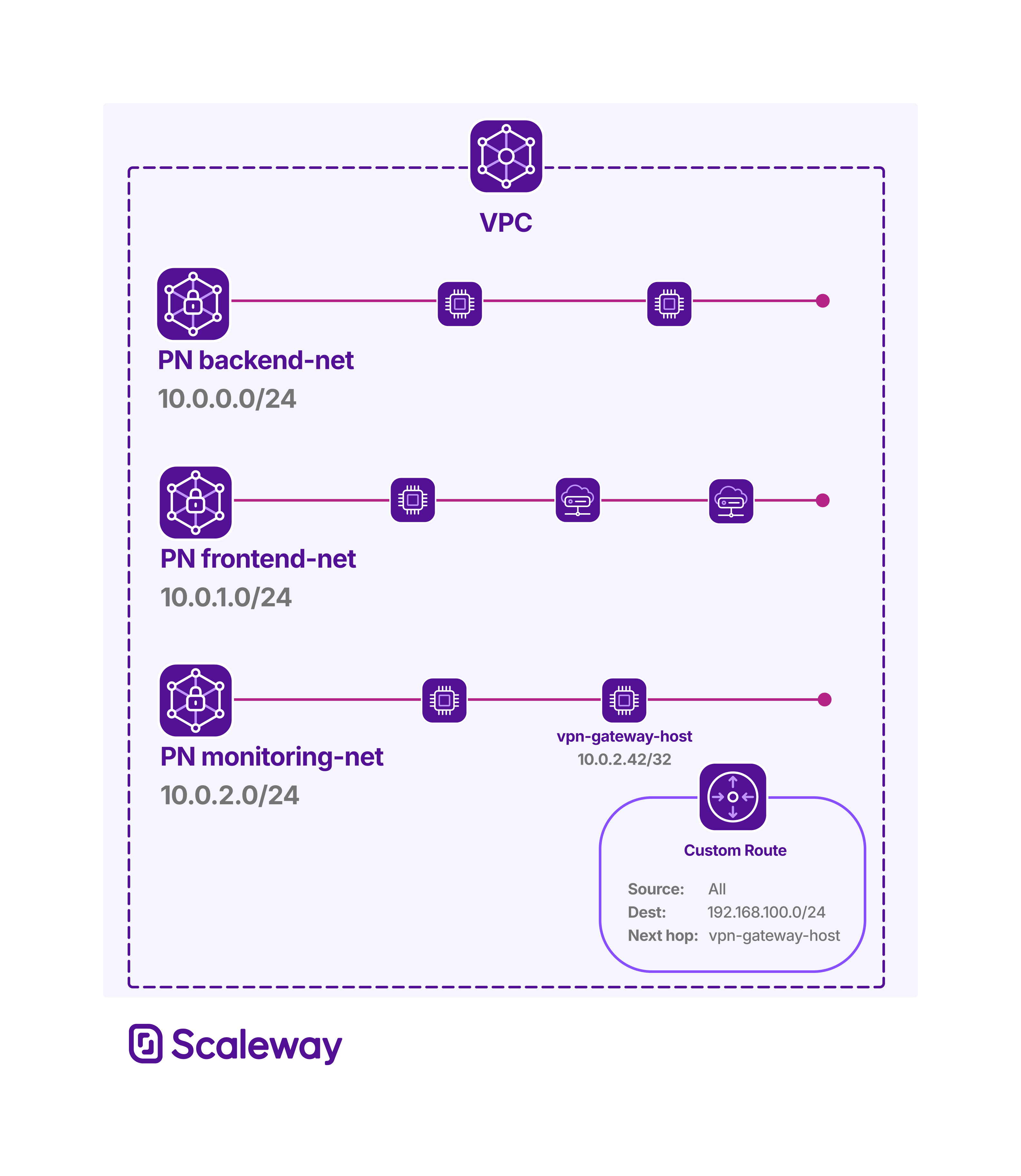
Your VPC has three Private Networks using the following CIDR blocks:
backend-net:10.0.0.0/24frontend-net10.0.1.0/24monitoring-net:10.0.2.0/24
There is a custom route configured in your VPC, that routes all source traffic destined for 192.168.100.0/24 to the Instance vpn-gateway-host as next hop. This Instance hosts a VPN gateway, and is attached only to Private Network monitoring-net, with the private IP address 10.0.2.42/32.
Problem
You want to prevent resources attached to backend-net and frontend-net from sending traffic to this VPN gateway, under new routing behavior where custom routes are advertised throughout the VPC. You want only resources attached to monitoring-net to be able to send traffic to the VPN gateway.
Solution 1: NACL allow
You could create two NACL rules to Deny traffic first from 10.0.0.0/24 (backend-net) and then from 10.0.0.1/24 (frontend-net) towards destination 10.0.2.42/32 (vpn-gateway-host). When combined with a default NACL rule to Allow all other traffic, this would effectively block resources on backend-net and frontend-net from accessing vpn-gateway-host.
Solution 2: NACL deny
Alternatively, and aligned with best practice, when the default NACL rule Denies all traffic not matched to a specific rule, backend-net and frontend-net will already be blocked from sending traffic to vpn-gateway-host on monitoring-net. Since NACLs do not filter traffic between resources attached to the same Private Network, other resources on monitoring-net would still be able to successfully route traffic to vpn-gateway-host.
Limitations
- Managed Databases are not currently compatible with routing. The VPC cannot automatically route between Managed Databases on different Private Networks, or (for example) between a Managed Database on one Private Network and an Instance on a different Private Network.
- VPC routing does not currently support virtual IPs.