Bucket policies overview
What are bucket policies
A bucket policy is a resource-based policy option. It allows you to grant more granular access to Object Storage resources.
By default, all Object Storage resources in a Project are private and can be accessed only by users or applications with IAM permissions. Adding a bucket policy to a bucket allows you to specify who can perform which actions on a bucket and the objects it contains. You can combine the different elements of a bucket policy to tailor your permissions according to your use case.
The different elements of a bucket policy allow you to configure fine-grained permissions when combined with Identity and Access Management (IAM), as shown in the table below.
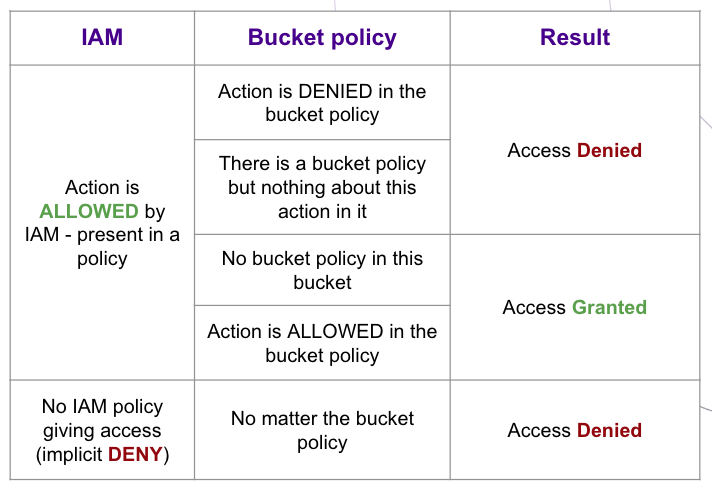
Bucket policies behave like objects: they can be uploaded into buckets. Once you upload, or "put" a bucket policy into a bucket, it takes immediate effect and will from then on define who can access and perform actions on the bucket, and the objects it contains.
Bucket policies versions
| Version ID | Lifecycle status |
|---|---|
2023-04-17 | Current |
2012-10-17 | Deprecated |
-
The
2012-10-17version is deprecated, and its usage is strongly discouraged. -
With the
2023-04-17version, only actions explicitly allowed by the bucket policy are permitted, if the principal is also allowed by an IAM policy. Deny statements are therefore useless.
Bucket policies description
Bucket policies use a JSON-based access policy language, and are composed of strings, such as: Version, Id, Statement, Sid, Principal, Action, Effect, Resource, and Condition.
Version
- Description
- IAM syntax version
- Required
- Yes
- Type
- string
- Value
"2023-04-17"
Sample:
{
"Version": "2023-04-17",
"Id": "MyBucketPolicy",
"Statement": [
{
"Sid": "Delegate access",
"Effect":"Allow",
"Principal": {
"SCW": "user_id:<USER_ID>"
},
"Action": "s3:ListBucket",
"Resource": "<BUCKET_NAME>"
}
]
}Id
- Description
- Information about the policy as a whole. The length is limited to 280 characters.
- Required
- No
- Type
- string
Sample
{
"Version": "2023-04-17",
"Id": "MyBucketPolicy",
"Statement": [
{
"Sid": "Delegate access",
"Effect":"Allow",
"Principal":{
"SCW":"application_id:<APPLICATION_ID>"
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}Statement
- Description
Statementdefines the rules that should be respected by our policy engine.- Children
Sid,Principal,Action,EffectandResource- Required
- No
- Type
- array
Samples
{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Delegate access",
"Effect":"Allow",
"Principal":{
"SCW":"user_id:<USER_ID>"
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
},
{
"Sid": "Delegate PUT to application",
"Effect":"Allow",
"Principal":{
"SCW":"application_id:<APPLICATION_ID>"
},
"Action":"s3:PutObject",
"Resource":"<BUCKET_NAME>/*"
}
]
}{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Delegate access to user",
"Effect":"Allow",
"Principal":{
"SCW":"user_id:<USER_ID>"
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
},
{
"Sid": "Delegate PUT to application",
"Effect":"Allow",
"Principal":{
"SCW":"application_id:<APPLICATION_ID>"
},
"Action":"s3:PutObject",
"Resource":"<BUCKET_NAME>/*"
}
]
}Sid
- Description
- Statement ID. Provides a way to include information about an individual statement.
- Required
- No
- Parent
- Statement
- Type
- string
Sample
{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant list to user",
"Effect":"Allow",
"Principal":{
"SCW":"user_id:<USER_ID>"
},
"Action":"s3:ListBucket",
"Resource":"<BUCKET_NAME>"
}
]
}Effect
- Description
- Uses the Allow value to authorize the specified actions. All actions that are not explicitly allowed are denied, Deny statements are therefore useless.
- Required
- Yes
- Parent
Statement
Sample
{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user and application",
"Effect":"Allow",
"Principal":{
"SCW":[
"user_id:<USER_ID>",
"application_id:<APPLICATION_ID>"
]
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}Principal
- Description
- Defines the targets of the bucket policy, which can be a user or an application. You must use
user_idand/orapplication_id, or*to grant access to "everyone". - Required
- Yes
- Parent
Statement
Sample
{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to everyone",
"Effect":"Allow",
"Principal":"*",
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user",
"Effect":"Allow",
"Principal":{
"SCW":"user_id:<USER_ID>"
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user and application",
"Effect":"Allow",
"Principal":{
"SCW":[
"user_id:<USER_ID>",
"application_id:<APPLICATION_ID>"
]
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}Action
- Description
- Consists of an Amazon S3 namespace, a colon, and the name of an action. Refer to the list below for supported actions.
- Required
- Yes
- Parent
Statement
Sample
{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user and application",
"Effect":"Allow",
"Principal":{
"SCW":[
"user_id:<USER_ID>",
"application_id:<APPLICATION_ID>"
]
},
"Action":"*",
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}Supported actions
To view the bucket policy action corresponding to each Object Storage API operation, refer to the dedicated documentation.
Supported global actions
*s3:*
Supported bucket actions
s3:DeleteBucketWebsites3:GetBucketAcls3:GetBucketCORSs3:GetBucketLocations3:GetBucketObjectLockConfigurations3:GetBucketTaggings3:GetBucketVersionings3:GetBucketWebsites3:GetLifecycleConfigurations3:ListBuckets3:ListBucketMultipartUploadss3:ListBucketVersionss3:PutBucketAcls3:PutBucketCORSs3:PutBucketObjectLockConfigurations3:PutBucketTaggings3:PutBucketVersionings3:PutBucketWebsites3:PutLifecycleConfiguration
Supported object actions
s3:AbortMultipartUploads3:DeleteObjects3:DeleteObjectTaggings3:DeleteObjectVersions3:DeleteObjectVersionTaggings3:GetObjects3:GetObjectAcls3:GetObjectLegalHolds3:GetObjectRetentions3:GetObjectTaggings3:GetObjectVersions3:GetObjectVersionTaggings3:ListMultipartUploadPartss3:PutObjects3:PutObjectAcls3:PutObjectLegalHolds3:PutObjectRetentions3:PutObjectTaggings3:PutObjectVersionTaggings3:RestoreObject
Resource
- Description
- Consists in the Amazon S3 resource path.
- Required
- Yes
- Parent
Statement
Sample
<BUCKET_NAME>- Grants access to the bucket, but not to the objects inside. If thes3:ListBucketaction is applied, this resource specification is required.<BUCKET_NAME>/*- Grants access to all objects inside a bucket, but not to the bucket itself. If thes3:PutObject,s3:GetObjectands3:DeleteObjectactions are applied, this resource specification is required.<BUCKET_NAME>/<PREFIX>/*- Grants access only to objects with the specified prefix inside a bucket, but not to the bucket itself.
{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user and application",
"Effect":"Allow",
"Principal":{
"SCW":[
"user_id:<USER_ID>",
"application_id:<APPLICATION_ID>"
]
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/*"
]
}
]
}{
"Version": "2023-04-17",
"Id":"MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user and application",
"Effect":"Allow",
"Principal":{
"SCW":[
"user_id:<USER_ID>",
"application_id:<APPLICATION_ID>"
]
},
"Action":[
"s3:ListBucket",
"s3:GetObject"
],
"Resource":[
"<BUCKET_NAME>",
"<BUCKET_NAME>/photos/*"
]
}
]
}Condition
- Description
- The
Conditionelement allows you to specify conditions for when a Policy is in effect. - Required
- No
- Parent
Statement- Condition keys
aws:SourceIp,aws:Referer,aws:CurrentTime,aws:EpochTime,s3:prefix
Examples
- You can use the
IpAddresscondition toAllowactions for specific IP ranges or addresses.
{
"Version": "2023-04-17",
"Id": "MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET from my Instances",
"Effect": "Allow",
"Principal": "*",
"Action": ["s3:ListBucket", "s3:GetObject"],
"Resource": ["<BUCKET_NAME>", "<BUCKET_NAME>/*"],
"Condition": {
"IpAddress": {
"aws:SourceIp": "192.0.2.0/24"
}
}
}
]
}- You can allow access only within a set timeframe, by implementing the
DateGreaterThanandDateLessThanconditions.
{
"Version": "2023-04-17",
"Id": "MyBucketPolicy",
"Statement": [
{
"Sid": "Grant List and GET to user for 10 years",
"Effect": "Allow",
"Principal": {
"SCW": "user_id:<USER_ID>"
},
"Action": ["s3:ListBucket", "s3:GetObject"],
"Resource": ["<BUCKET_NAME>", "<BUCKET_NAME>/photos/*"],
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2020-01-01T00:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2030-01-01T00:00:00Z"
}
}
}
]
}- You can also allow access according to the
HTTPreferer.
{
"Version": "2023-04-17",
"Id": "MyBucketPolicy",
"Statement": [
{
"Sid": "Allow access to assets from my website",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": ["<BUCKET_NAME>/assets/*"],
"Condition": {
"StringLike": {
"aws:Referer": "https://console.scaleway.com/*"
}
}
}
]
}Supported conditions
IpAddressNotIpAddressStringEqualsStringNotEqualsStringEqualsIgnoreCaseStringNotEqualsIgnoreCaseStringLikeStringNotLikeDateGreaterThanDateGreaterThanEqualsDateLessThanDateLessThanEquals
Refer to our dedicated documentation for more information on managing bucket permissions for IP addresses or ranges of IP.