SSL/TLS Certificates for Edge Services
This document contains information to help you with SSL/TLS certificates that enable your origin bucket or Load Balancer content to be served over HTTPS, through your customized Edge Services domain.
Introduction
What is an SSL/TLS certificate?
An SSL/TLS certificate is a digital certificate that enables an encrypted connection between a client and a web server over HTTPS.
You may hear certificates referred to as “SSL certificates”, “TLS certificates” or “SSL/TLS certificates”. These are all the same thing. SSL (Secured Socket Layer) was the protocol initially used for encryption, though it has now been replaced with TLS (Transport Layer Security).
SSL/TLS certificates contain a public key, which corresponds to a separate private key. These work as a pair. When a client wants to establish an encrypted connection to a host, it requests the host's certificate. The host shares the certificate, which includes the public key (the private key is never shared and is kept by the host). The client checks the certificate, and uses the host's public key to encrypt the data that it transfers to the host. The host uses its private key to decrypt the data that has been encrypted by the public key.
The private key is also used by the host for generating digital signatures, while the public key is used by clients for verifying those signatures.
When and why do I need an SSL/TLS certificate for Edge Services?
When you create an Edge Services pipeline, initially your origin's content is served through the standard Edge Services endpoint, e.g. https://pipeline-id.svc.edge.scw.cloud. Scaleway's own SSL/TLS certificate, which covers this subdomain, is used to establish the encrypted connection between client and host. If you do not want to customize the standard Edge Services endpoint, you do not need to worry about creating SSL/TLS certificates.
However, if you choose to customize your Edge Services endpoint with your own subdomain, Scaleway's own SSL/TLS certificate can no longer be used to establish encrypted connections to your subdomain. Client connections are now initially going to a different domain which needs to be "guaranteed" by its own certificate (despite the CNAME record for the subdomain pointing to the Scaleway endpoint).
Therefore, when you customize your Edge Services endpoint with a subdomain, you are prompted to generate or upload an SSL/TLS certificate for that subdomain.
How can I provide an SSL/TLS certificate for my Edge Services customized domain?
You will be prompted to choose one of the following options when customizing your domain:
-
Generate a Let's Encrypt certificate: Scaleway generates a free, managed Let's Encrypt certificate for your domain and automatically renews it as necessary.
-
Select an existing certificate from Secret Manager: You select a certificate that you have already uploaded in Scaleway Secret Manager.
-
Manually import a certificate into Secret Manager: You can manually create your own certificate and import it. It will be stored in Scaleway Secret Manager (check the dedicated pricing page).
Generating a managed Let's Encrypt certificate
This is the hassle-free option if you do not want to create or manage your own SSL/TLS certificate. Scaleway takes care of generating a certificate for your customized domain in the correct format. The certificate is automatically renewed before it expires. This option is available for free: it costs you nothing for Scaleway to generate and manage a Let's Encrypt certificate for your domain.
You must ensure that you have correctly set the CNAME record for your domain. Without having done this, the Let's Encrypt certificate option in the console will not be available. It is also important to check the CNAME is correctly set up so that the certificate is properly generated and reviewed.
Note that you will not have access to the generated certificate itself in Secret Manager or elsewhere. It is entirely generated and managed "behind the scenes", and is not configurable by the user. If you reset your domain, or delete your Edge Services, Scaleway automatically deletes the generated Let's Encrypt certificate.
Troubleshooting Let's Encrypt certificate errors
See our dedicated documentation for help resolving errors experienced when generating or renewing an Edge Services Let's Encrypt certificate.
Using your own certificate
If you wish to use your own certificate, rather than the option of generating a managed Let's Encrypt certificate, take into account the following points.
Accepted certificate types
Types of validation:
- ❌ Self-signed certificates. Certificates for Edge Services must be signed by a trusted Certificate Authority (CA)
- ✅ Domain Validated Certificate. The CA simply checks that the applicant owns the domain.
- ✅ Extended/Organization Validation Certificate. The applicant must pass more in-depth validation procedures and checks by the CA.
Types of domain coverage:
- ✅ Single domain certificate. Secures a single domain or subdomain. Note that the certificate must be for
your-sub.domain.com, where the subdomain corresponds to the subdomain for Edge Services. A single domain certificate simply foryourdomain.comwould not be acceptable, as it would not cover the subdomain for Edge Services. - ✅ Wildcard certificate. Secures multiple subdomains for a domain, using a wildcard
*symbol. The Common Name of the certificate should look like*.yourdomain.com. - ✅ Multi-domain (MD) / Subject Alternative Name (SAN) / Unified Communications Certificate (UCC) certificate. Secures multiple explicitly-defined fully qualified domain names (
www.yourfirstdomain.com,sub.yourfirstdomain.com,yourfirstdomain.com,yourseconddomain.com,sub.yourseconddomain.cometc.)
PEM format certificate chain
Edge Services requires that you import your certificate as a PEM-formatted certificate chain, which includes the private key. PEM format is Base64 encoded ASCII, and by definition includes lines stating -----BEGIN x----- and -----END x-----.
Your PEM formatted certificate chain should look like this:
-----BEGIN PRIVATE KEY-----
(private key here)
-----END PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
(primary certificate (aka server certificate) here)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(intermediate certificate here)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(root certificate here)
-----END CERTIFICATE-----| Section | Contains | Subject (issued for) | Issued and signed by |
|---|---|---|---|
| Private key | The private key file for the certificate | ||
| Primary/server certificate | The certificate issued by the CA for your domain name | Your name and public key | CA |
| Intermediate certificate | The intermediate certificate chaining your primary certificate to the root certificate | CA's name and public key. | Root CA |
| Root certificate | The root certificate by the CA, for the trusted CA itself | The Root CA's name and public key | Root CA (self signed) |
Note that in certain cases an intermediate certificate may not be necessary, if the root certificate chains directly to the primary/server certificate. The crucial thing is that the subject and issuers of each certificate form a coherent chain of validation. If a certificate is issued by an authority that is not present in the chain, an error will occur.
Tips for creating a certificate
In general, SSL/TLS certificates can either be self-signed (signed by the subject of the certificate, e.g. the owner of the domain) or CA-signed (signed by a third party Certificate Authority which is publicly trusted).
Self-signed certificates cannot be used with Edge Services, all certificates must be signed by a CA that is known and trusted by Edge Services.
To get an SSL/TLS certificate for your domain or subdomain, you need to generate a Certificate Signing Request (CSR) and submit it to a Certificate Authority (CA) for them to validate your domain, who then send you a signed certificate. You may be able to carry out this procedure via your hosting provider, or from the command line.
CAs of private companies whose primary business is not SSL or domains may not be trusted by Edge Services. If you encounter a self-signed certificate error with Edge Services, but you believe your certificate is legitimately signed by an official CA, open a support ticket to tell us.
Uploading your certificate
When you configure your customized domain with Edge Services for the first time, you are prompted to upload your certificate. You can do so in two ways:
- Select an existing certificate that you have stored in a secret in Scaleway Secret Manager. The secret must be of the certificate type in order to be visible to Edge Services. The type can be defined when creating a secret via the API, but not via the console. For that reason, if you prefer to use the console to create your certificates, we suggest using the next option:
- Manually import a certificate into Scaleway Secret Manager, directly from the Edge Services Configure domain wizard (copy and paste the PEM formatted chain). Your certificate will be automatically stored in Secret Manager, held in a secret that automatically inherits the type "certificate".
Keeping your certificate up to date
SSL/TLS certificates all expire at some point. If your certificate expires before you upload a new one, you will see an error like this on your Edge Services dashboard:
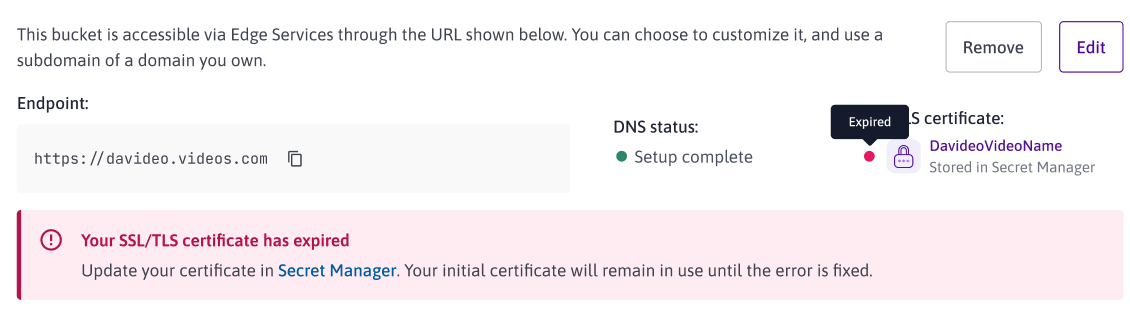
You must renew your certificate or create a new one. A number of tools are available to ensure that certificates are automatically renewed before expiry, for example Certbot for LetsEncrypt. However, since Certbot or other tools for automatically renewing certificates are not currently integrated into Edge Services, you will need to manually update the certificate via the Scaleway console.
When you have your up to date certificate, go to Secret Manager in the console, and access the secret that contains your certificate. Create a new version of the secret, to hold the up to date certificate. Edge Services will automatically detect and use the most recent enabled version of the secret. You can nonetheless choose to disable or delete the old version(s) as you prefer, which will also save your billing costs (since you are billed per version).
Troubleshooting certificate errors
See our dedicated documentation for help resolving errors associated with your custom certificate for Edge Services.