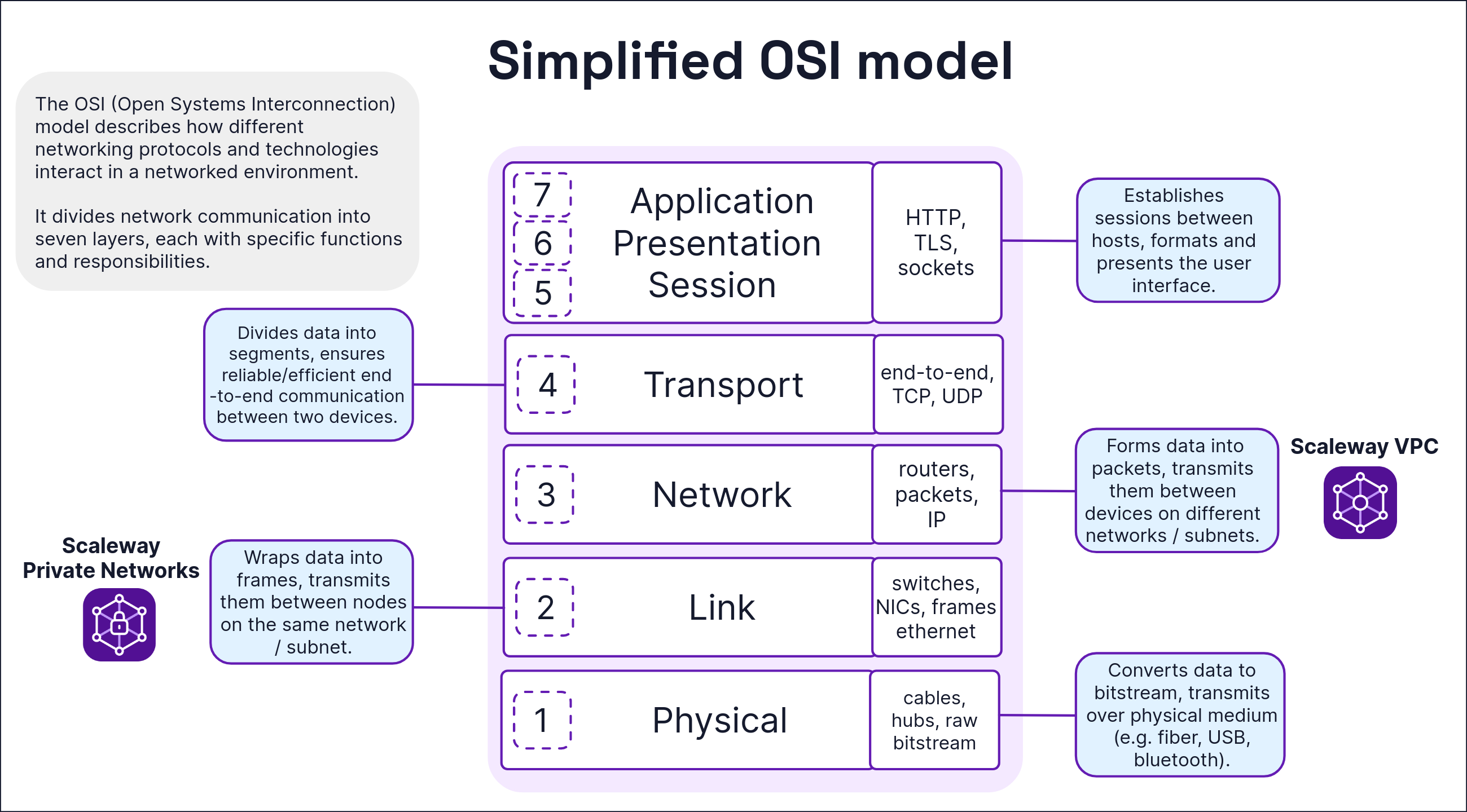
VPC - Concepts
CIDR block
An IPv4 CIDR block and an IPv6 CIDR block are defined for each Scaleway Private Network at the time of creation. When you attach a resource (e.g. an Instance) to the network, DHCP will assign one IPv4 and (if the resource is IPv6-compatible) one IPv6 address from the designated blocks to that resource.
Classless Inter-Domain Routing (CIDR) blocks represent a range of IP addresses sharing the same network prefix. An example of an IPv4 CIDR block is 172.16.16.0/22, while an IPv6 CIDR block looks like fd12:3456:789a:1::/64.
- The prefix of the CIDR block (e.g.
172.16.16.0) represents the network address, and the starting point of the IP address range. - The suffix of the CIDR block (e.g.
/22) represents the network size. This is also known as the prefix length or subnet mask bit size. It states how many bits of the prefix are used to designate the network itself, with the remaining bits therefore being available to designate specific hosts on the network.
Default VPC
Projects created before 13 May 2025
- One default VPC was automatically created for each region (Paris, Amsterdam and Warsaw).
- You can now choose to delete one or all of your default VPCs. If you do, the behavior for newer Projects described below will apply.
Projects created after 13 May 2025
-
Default VPCs are no longer automatically created for you.
- Console:
- The concept of default VPCs is no longer needed or relevant.
- You must create a VPC for a given region before you can create a Private Network in that region.
- You are prompted to specify a VPC every time you create a Private Network.
- API:
- The
is_defaultfield continues to exist, and as before, it cannot be updated or set by the user. - If you create your own VPCs, and always specify one of them when creating a Private Network, none of your VPCs will be flagged as
is_default. - When you create a Private Network in a given Project/region without specifying a pre-existing VPC for the first time, a VPC is auto-created for you and designated as default for the Project/region via the
is_defaultflag. - Any further Private Networks that you create in that Project/region without specifying a VPC will be added to the auto-created
is_defaultVPC. - User-created VPCs cannot be set as default.
- The
- Console:
DHCP
Dynamic Host Configuration Protocol (DHCP) is a network management protocol for dynamically assigning IP addresses and other configuration parameters to devices in a Private Network.
Managed DHCP was previously a feature of Scaleway's Public Gateway, but is now built into Private Networks. A CIDR block representing a range of available IP addresses is defined when creating the Private Network, and when you attach a resource to the network it is assigned a static, private IP address from this subnet. These IP addresses are managed by our internal IPAM, which acts a single source of truth and ensures full consistency. There is no need for users to manually assign private IP addresses to their resources as they join or leave the network. However, you can choose to assign particular reserved IP addresses if you wish.
Even with automatic IP address assignment, thanks to managed DHCP, a resource's IP address will never change as long as that resource is not detached from the Private Network. It remains stable across reboots and long poweroffs. The IP is allocated when the resource is attached, and released only when the resource is detached or deleted.
The IPv4 address of Private Networks' DHCP server is 169.254.169.254. The IPv6 address is fe80:200:22ff:fe05:ca1e.
DNS
The Domain Name System (DNS) is a naming system for devices connected to the internet or Private Networks. Most prominently, DNS servers translate text-based domain names (e.g. www.scaleway.com) to numerical IP addresses (e.g. 51.158.66.220).
Scaleway Private Networks benefit from managed DNS, which resolves the hostnames of attached resources into their IP addresses. The hostname for a given device is generally the name defined when creating the resource (and which in the case of an Instance, for example, displays in the shell when connected to that resource by SSH). See full information on Scaleway DNS and how to reach a resource via its hostname.
IPAM
IP Address Manager (IPAM) is Scaleway's tool for planning, tracking and managing the IP address space of Scaleway products. It acts as a single source of truth for the IP addresses of Scaleway resources. See our dedicated IPAM documentation for full information.
IPv4
Internet Protocol Version 4 is the standard protocol used for IP addresses. Composed of 32 bits, when written in human-readable form an IPv4 address is generally shown as four octets separated by periods, e.g. 151.115.59.87.
When a resource is attached to a Private Network, it has a private IPv4 address on that network. Scaleway Private Networks' DHCP functionality assigns this private IPv4 address (as well as an IPv6 address, if the resource is IPv6-compatible) when the resource joins the network. Alternatively you can reserve and attach an IP address of your choice with IPAM.
IPv6
Internet Protocol Version 6 is the most recent version of the IP protocol used for IP addresses. Composed of 128 bits, written in human-readable form, an IPv6 address can be shown as eight groups of four hexadecimal digits separated by a colon, e.g. 2001:0DB8:0000:0003:0000:01FF:0000:002E. This can also be notated as 2001:DB8::3:0:1FF:0:2E.
When an IPv6-compatible resource is attached to a Private Network, it has a private IPv6 address on that network. Scaleway Private Networks' DHCP functionality assigns this private IPv6 address when the resource joins the network. Alternatively you can reserve and attach an IP address of your choice with IPAM.
Network ACL
A VPC's Network Access Ccontrol List is composed of stateless rules to control the flow of traffic between Private Networks. By default, the list contains no rules, and therefore traffic is allowed to flow unrestrictedly between the VPC's Private Networks. Add rules to the list to start creating restrictions. Take a deeper dive into NACLs.
Private IP address
A private IP address identifies a resource on a Private Network. When you attach a resource (e.g. an Instance) to the network, you can either use a reserved IP address, or let DHCP assign one IPv4 and (if the resource is IPv6-compatible) one IPv6 address from the designated CIDR blocks to that resource.
For example, a private IPv4 address may resemble 172.16.16.2/22. This format encapsulates information both about the resource's IP address, and also the subnet (Private Network) itself. If you configure an Instance manually with this address, it sets both the correct IP and a route to the correct subnet.
Private Networks
Private Networks let you connect Scaleway resources across multiple AZs within the same region. Attached resources can then communicate between themselves in an isolated and secure layer 2 network, away from the public internet.
Dynamic Host Configuration Protocol (DHCP) is built into each Private Network, making it easy to manage the private IP addresses of your resources on the network.
Read our dedicated documentation on creating a Private Network.
Region and Availability Zone
A region is a geographical area, such as France (Paris: fr-par) or the Netherlands (Amsterdam: nl-ams), in which Scaleway products and resources are located. It can contain multiple Availability Zones.
An Availability Zone refers to the geographical location within a region, such as waw-1 (Warsaw, Poland), in which your Scaleway resource will be created. The latency between multiple AZs of the same region is low, as they have a common network layer.
For an extensive list of which regions and AZ a resource is available in, refer to our Product availability guide.
Route table
A route table is used to manage and control the routing of traffic within a VPC. The routes within a route table tell the VPC where to send traffic trying to get to a specific destination IP address. One line in the route table corresponds to one route.
Routes can be of the following types:
- Auto-generated, fully managed
Local subnet routesfor routes to Private Networks. - Auto-generated, fully managed
Default route to internetfor routes to Public Gateways. - Custom routes created by the user.
When deciding which route to apply, the route table reads the routes from most specific to least specific, in terms of destination IP range. The first matching route encountered is the one that determines the path for the traffic. Therefore, a route to destination 172.16.8.0/22 is applied before a default route to 0.0.0.0/0.
Each route in a route table has a scope: it may be advertised across the entire VPC, or on certain Private Networks only.
Routing
Routing allows resources on Private Networks within the same VPC to communicate with each other, via managed and custom routes. Routing is activated by default whenever you create a new VPC, and can be activated on pre-existing VPCs by following these steps.
Each routed VPC has a route table which is automatically populated with routes to each of its Private Networks. When you attach a Public Gateway to a Private Network, and tell it to advertise a default route to the internet, such routes are also added to the VPC's route table. You can also create your own custom routes, to route traffic towards defined destination IP ranges towards specific "next hop" resources.
Read more about how routing works in our detailed guide.
vRouter
A vRouter is a virtualized router that sits inside a VPC and manages layer 3 routing between its resources. It holds the route table for the VPC. A VPC's vRouter is entirely managed by Scaleway, and not directly configurable by the user.
VPC
VPC allows you to build your own Virtual Private Cloud on top of Scaleway's shared public cloud. Within each VPC, you can create Private Networks and attach Scaleway resources to them, as long as the resources are in an AZ within the network's region.
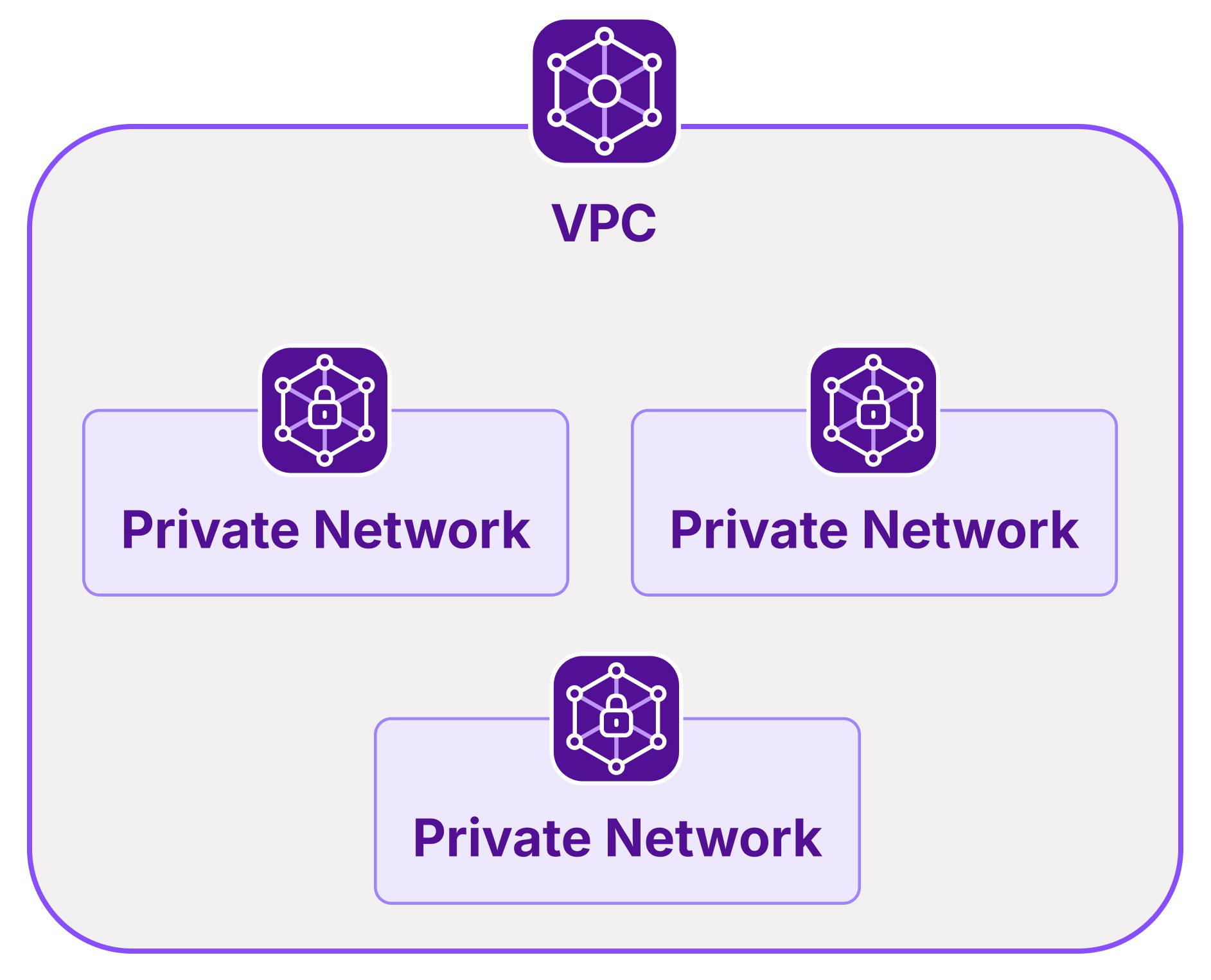
VPC currently comprises the Private Networks product. Layer 2 Private Networks sit inside the layer 3 VPC. VPC routing allows traffic to be routed throughout the VPC.
Find out more about getting the most from your VPC and Private Networks.