Understanding Site-to-Site VPN
Site-to-Site VPN overview
Site-to-Site VPN lets you securely connect your Scaleway VPC to your remote infrastructure, enabling encrypted data exchange over a private VPN tunnel. Integrated with VPC routing, traffic destined for your remote infrastructure can reach it from your VPC via the secure VPN tunnel, and vice versa. Site-to-Site VPN connections are secured with Internet Protocol security (IPsec).
Components of Site-to-Site VPN
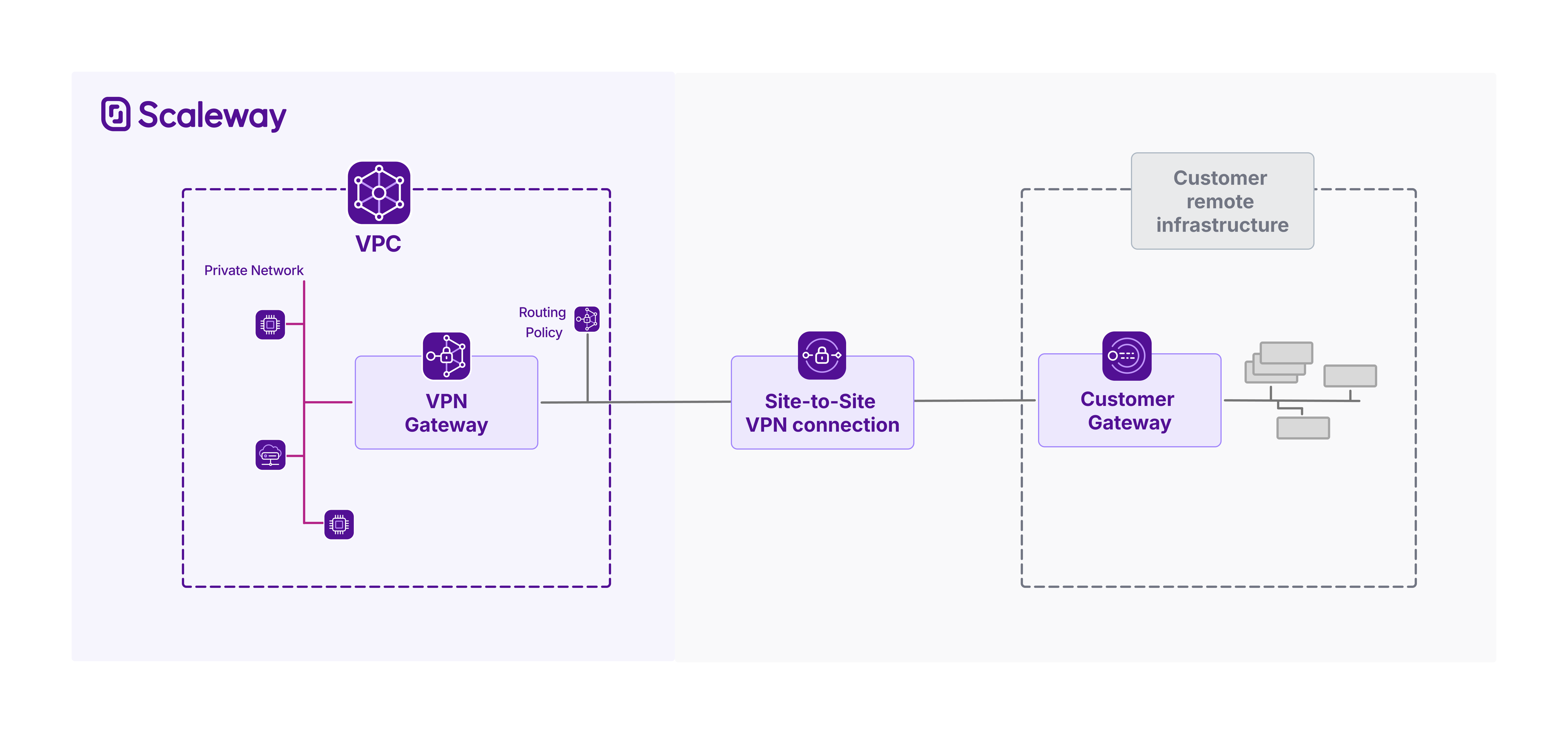
Scaleway Site-to-Site VPN consists of:
- A VPN gateway: the connection point on the Scaleway side
- A customer gateway: the connection point on the remote side (representing a corresponding physical customer gateway device)
- A routing policy: defines the traffic allowed to flow through the tunnel
- A connection: brings together the three above elements, and defines the configuration for the VPN tunnel
You must create all of the above elements, and correctly configure your customer gateway device, for a functional Site-to-Site VPN.
VPN gateway
The VPN gateway provides a connection point on the Scaleway side of a Site-to-Site VPN tunnel. It has the following properties, which you can customize when you create the gateway:
- Region: The geographical location in which the gateway is created. It must be in the same region as the other Site-to-Site VPN resources (customer gateways, routing policies, connections) that you want to use it with.
- Name and (optionally) tags: A name and tags to identify the gateway.
- Gateway type: Different gateway types are available for different prices. Pricing is based on bandwidth, and the maximum number of connections the gateway can be used for.
- Private Network: Each gateway must be attached to a single Scaleway Private Network. The network chosen cannot be modified after creation of the gateway. The gateway will get both an IPv4 and IPv6 address on the Private Network. Other Private Networks in the VPC will be able to learn the route through the VPN gateway.
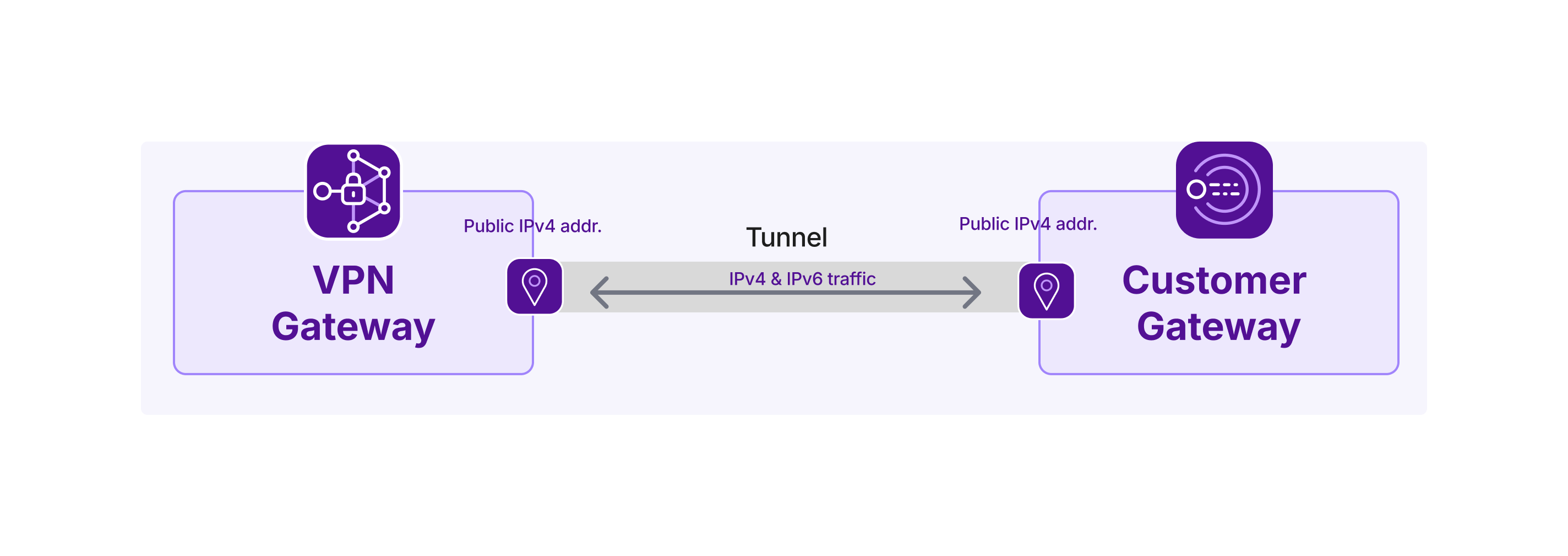
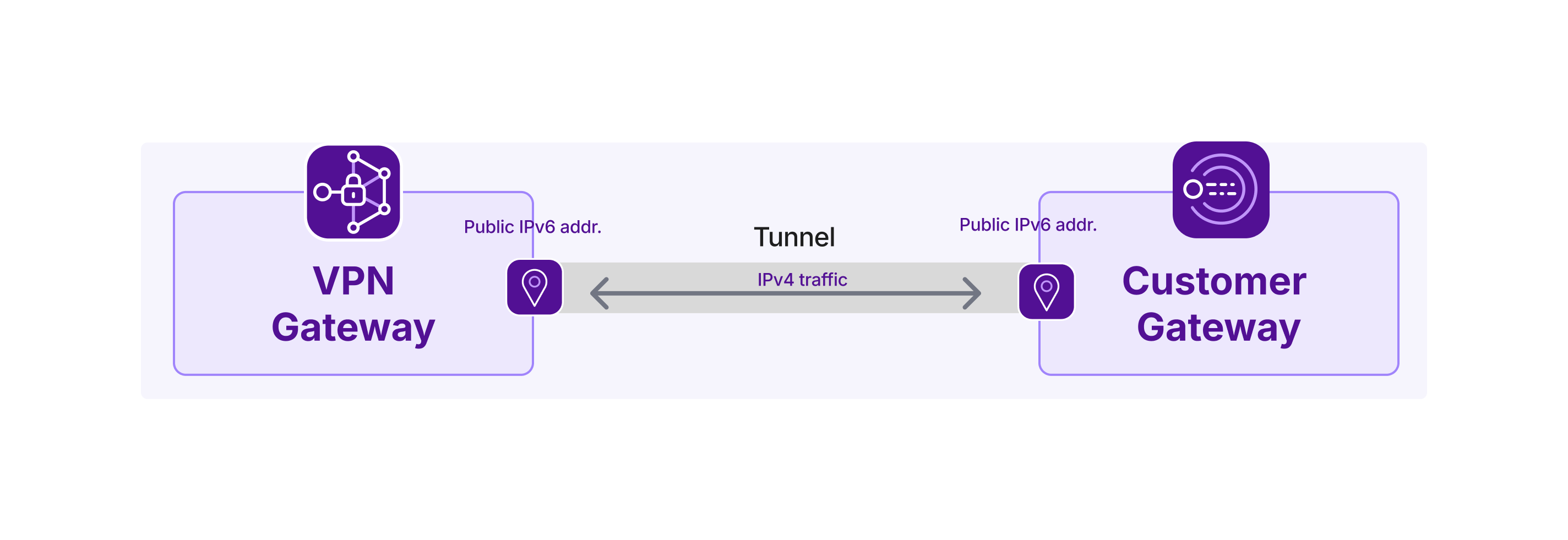
- Public IP address(es): The address(es) used to establish the VPN tunnel. Maximum of one IPv4 /32 and one IPv6 /128 address per gateway. VPN gateways with both types of IP will be able to support two connections to a single customer gateway, corresponding to one IPv4 tunnel and one IPv6 tunnel, providing increased redundancy.
Customer gateway
The customer gateway provides a connection point on the customer (remote) side of a Site-to-Site VPN tunnel. It is the logical representation of a real customer gateway device, a physical or software-based networking device.
A customer gateway has the following properties, which you can customize when you create the gateway:
- Region: The geographical location in which the gateway object is created. It must be in the same region as the other Site-to-Site VPN resources (VPN gateways, routing policies, connections) that you want to use it with.
- Name and (optionally) tags: A name and tags to identify the gateway.
The rest of the properties must correspond to the real properties of the corresponding real customer gateway device:
-
Public IP address: The address(es) used to establish the VPN tunnel. Maximum of one IPv4 and one IPv6 address per gateway. Customer gateways with both types of IP will be able to support two connections to a single VPN gateway, corresponding to one IPv4 tunnel and one IPv6 tunnel, providing increased redundancy.
-
Autonomous System Number (ASN): The unique identifier assigned to the customer's network, used by BGP (Border Gateway Protocol) to exchange routing information with other networks.
Routing policy
By default, when you create a VPN connection, all routes across it are blocked. You must create and attach a routing policy for the connection, which sets filters for the IP prefixes to allow.
A VPN connection must have a minimum of one and a maximum of two attached routing policies, one for each IP traffic type to be routed (IPv4 and/or IPv6).
A routing policy has the following properties, which you can customize when you create the policy:
- Region: The geographical location in which the routing policy is created. It must be in the same region as the other Site-to-Site VPN resources (VPN gateways, customer gateways, connections) that you want to use it with.
- Traffic type: IPv4 or IPv6. If a VPN connection is to support both IPv4 and IPv6 traffic, it needs one routing policy per traffic type.
- Name and (optionally) tags: A name and tags to identify the policy.
You can whitelist multiple outgoing routes and multiple incoming routes per policy.
- Outgoing routes are the IP prefixes that define ranges of Scaleway VPC route announcements to whitelist. Routes within these destinations will be propagated, allowing traffic from the remote gateway to be routed via the VPN to your VPC.
- Incoming routes are the IP prefixes that define ranges of route announcements from the customer gateway to whitelist. Routes towards these destinations will be propagated, allowing traffic from the Scaleway VPC to be routed via the VPN to your remote infrastructure.
Connection
A connection represents the configuration of a secure link between a VPN gateway and a customer gateway. It defines all the characteristics of the Site-to-Site VPN tunnel, including routing policy and encryption method.
A connection has the following properties, which you can customize when you create the policy:
-
Region: The geographical location in which the connection is created. It must be in the same region as the other Site-to-Site VPN resources (VPN gateways, customer gateways, routing policies) that it uses.
-
Name and (optionally) tags: A name and tags to identify the policy.
-
VPN gateway: The VPN gateway to use for the connection.
-
Customer gateway: The customer gateway to use for the connection. It must have at least one public IP type in common with the VPN gateway (IPv4 and/or IPv6).
-
Tunnel details: Based on the gateways selected, you may need to define how the connection should establish the VPN tunnel between them.
- If both gateways have public IPv4 and public IPv6 addresses, you must explicitly choose the IP type (IPv4 or IPv6) to be used for the tunnel.
- If the gateways share only one public IP type, that IP type will be used automatically for the tunnel.
- A maximum of two connections can be created between the same gateway pair: one with an IPv4 tunnel and one with an IPv6 tunnel. Creating two connections/tunnels per gateway pair increases redundancy. Once an IPv4 tunnel is created, only one additional IPv6 tunnel can be established, and vice versa. No further connections are permitted beyond this limit.
-
Routing policy(ies): For each traffic type (IPv4 and/or IPv6) to be routed over the connection, an associated routing policy must be attached (see above).
-
Connection initiation policy: Which gateway should initiate the tunnel. This can be either the VPN gateway, or the customer gateway. The chosen gateway will be responsible for kicking off the secure exchange that sets up the IPsec tunnel.
-
Security proposal: Defines the encryption and authentication methods used to secure the VPN tunnel. For full details on available security proposals, see our dedicated documentation.
-
Pre-shared key (PSK): Generated automatically when you create the connection object. It is securely stored in Scaleway Secret Manager, and can be retrieved for the purposes of configuring your customer gateway device. For now, it is not possible to customize the PSK. You must use the auto-generated one.
Configuring your customer gateway device
After creating your Site-to-Site VPN connection, you are prompted to configure your customer gateway device.
Your customer gateway device is a real physical or software-based networking device, located on the remote network you want to connect to your Scaleway VPC. The customer gateway that you create in Scaleway is a logical representation of this device.
Scaleway cannot configure your device for you. In order to successfully complete the setup of your Site-to-Site VPN, you must configure the device yourself. You will need the following information, which is available from the API:
- Public IP address(es) of the VPN gateway: The IPv4 address, IPv6 address, or both, that you configured when creating the VPN gateway.
- Scaleway ASN: 12876
- Pre-shared key: Auto-generated for you upon creation of the connection, and stored in Scaleway Secret Manager
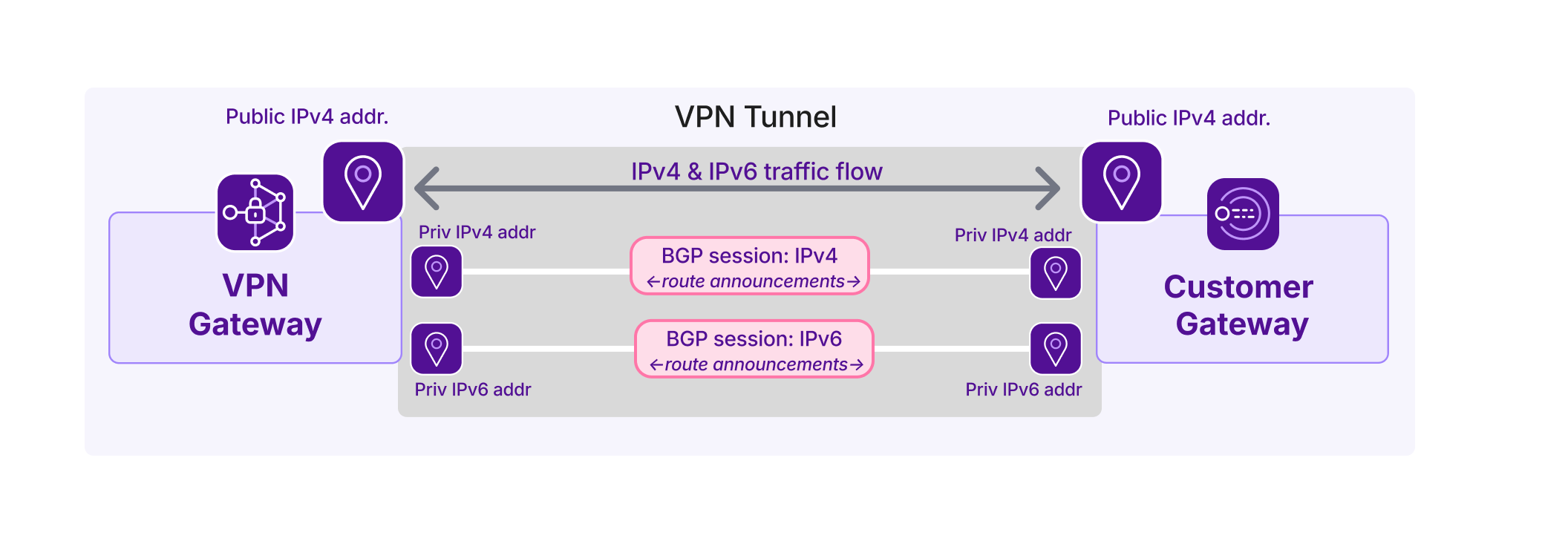
You also need to set up route announcements and filters on the customer side. For this, you will need the following information:
-
BGP interconnection subnet(s): The private subnet used to provide private IP addresses for the VPN gateway and customer gateway over the tunnel. The gateways connect over this private subnet to establish a BGP session and exchange routing information. For connections that are configured to route both IPv4 and IPv6 traffic, one IPv4 and one IPv6 subnet will be provided. Subnet information can be accessed via the API.
-
Routing policy: Take into account the routing policy(ies) you attached to the connection, when configuring routing policy on the customer gateway device.
BGP communities
You can influence routing between the various Site-to-Site VPNs in a VPC, for traffic flowing from Scaleway to your external network, by using BGP communities.
Refer to the BGP community documentation for InterLink for details - the same information applies for Site-to-Site VPN. Note that by default, InterLink takes priority over Site-to-Site VPN for equivalent routes.
Activating route propagation
The final step in allowing traffic to flow over your Site-to-Site VPN, is to activate route propagation. This enables all the allowed prefixes defined in the routing policy to be announced in the BGP session. Traffic cannot flow over the VPN when route propagation is not activated.
Activate route propagation via the dedicated call in the API.
Monitoring connection status
Once you have created your Site-to-Site VPN connection, and configured your customer gateway device, monitor the status of your connection. If your device is successfully configured, and the connection is working, the status should be Active.
See our dedicated status documentation for full information on different statuses for the VPN gateway and connection, and how to troubleshoot them.
VPC routing
Routes to your Site-to-Site VPN gateway are automatically added to your VPC's route table, and advertised to all Private Networks within the VPC. This allows all resources within your VPC to find the route through the VPN tunnel, to your remote infrastructure.
Use Network ACLs if you want to limit the resources that route traffic through the VPN gateway.
Site-to-Site VPN limitations
- Site-to-Site VPN is currently in Public Beta, and available only via the Scaleway API.
- You cannot use Site-to-Site VPN to connect two Scaleway VPCs
- You cannot modify the Private Network that a VPN is connected to after creation
- You must use the auto-generated pre-shared key (PSK) for a VPN connection: you cannot currently define your own PSK
- We cannot currently provide a configuration file for customer gateway devices